New security methodology for connected cars
Cars are getting smarter and more connected every day. But there’s a hitch — these computer systems on wheels are becoming a prime target for cyber criminals and hackers.
Thales has teamed with the PSA Group (makers of Peugeot and Citroën vehicles) to develop a methodology for identifying these risks and the measures that need to be taken to keep vehicles safe and secure.
Capable of exchanging information such as road and traffic conditions with other vehicles and devices in its own ecosystem — and possibly even driving themselves in the near future — this new breed of cars promises an enhanced driving experience and unprecedented levels of road safety. But the interconnected onboard systems of the future present carmakers with a whole new set of IT security challenges.
Hackers at the wheel
Vehicles today rely on onboard computers called ECUs, or electronic control units, which manage not just the in-car infotainment systems but also critical functions such as fuel injection and braking. And for the growing number of vehicles fitted with driving and parking aids, they can also control the steering.
New models sport a whole array of connectivity features, such as USB ports, GSM chips, Bluetooth and Wi-Fi capabilities, but hackers can potentially use these features to access the vehicle’s many onboard computers, which are currently about as secure as desktop computers were in the early days of the Internet.
One carmaker was the centre of media attention in July 2015 when security researchers conducted a spectacular demonstration, taking control of the vehicle from a remote location by exploiting a vulnerability in its onboard entertainment system. From a computer many miles away, they switched on the windscreen wipers, turned up the radio, slammed on the brakes, took control of the steering and then turned off the engine…
Another potential vulnerability is the web applications that send data between the vehicle and the manufacturer’s information system. If the authentication process isn’t secure enough, hackers could gain access to the user’s account and, from there, get their hands on the vehicle.
Added to that, it’s surprisingly easy for a thief to steal a vehicle by using tools that are readily available on the web to retrieve a car’s immobiliser code. These codes are stored on the corresponding ECU, with varying levels of security, and can be coded into a new blank key fob to start and steal the vehicle. French consumer group 40 Millions d’Automobilistes estimates that three-quarters of cars stolen in France in 2014 were electronically hacked.
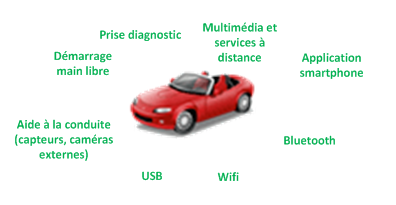
Diagram:
Entertainment and remote services
Smartphone application
Bluetooth
Wi-Fi
USB
Driving aids (external sensors, cameras)
Hands-free ignition
Diagnostic port
Tests by IT security engineers have repeatedly shown just how insecure today’s connected cars are, discovering that a significant proportion of vehicles from big-name manufacturers were vulnerable to attack. Increasingly, carmakers are coming to recognise the need to embrace the issues of security and authentication and to work with experts in this field.
Focused risk analysis
As a world leader in critical information systems, cybersecurity and data protection, Thales has joined forces with the PSA Group in France to develop a comprehensive, step-by-step methodology for assessing the security of onboard vehicle systems.
Experience shows that IT security must be taken into account at the earliest possible stage in the design and development process, if it’s to be effective, understood and affordable. Combining two complementary methods, a new risk analysis methodology has been specifically designed by Thales and the PSA Group for the automotive sector to identify security threats and the necessary countermeasures at the pre-specification phase.
Based on the EBIOS[1] model proposed by ANSSI, France’s national agency for information system security, and the TVRA[2] methodology from ETSI, the European Telecommunications Standards Institute, the method comprises five key stages:

Diagram:
Step 1: background study
Step 2: study of potential events
Step 3: TVRA risk study (technical risks)
Step 3a: assessment of likelihood of attack scenario
Step 3b: assessment of intensity of attack
Step 3c: assessment of impact of attack on the support asset
Step 3d: assessment of overall impact of attack
Correspondence matrix
Step 4: study of EBIOS risks (sector specific)
Step 5: study of security measures
By combining these two methods, it is possible to evaluate the risks of vehicle data being compromised in terms of confidentiality, integrity, availability and traceability, and to obtain a technical picture of the security architecture based on a comprehensive, detailed TVRA assessment (stage 3).
EBIOS risks are assessed by comparing the seriousness of each potential threat and how likely it is to happen.

Diagram:
Seriousness of potential events
4 Critical
3 Major
2 Moderate
1 Low
Likelihood of threat
4 Very likely
3 Likely
2 Rarely
1 Unlikely
Just another information system
Protecting an in-car system is ultimately the same as protecting any other kind of information system. Security measures could include perimeter security for the system concerned, for example, but may also need to address data protection, authentication between electronic components and protection of the operating system and the codes embedded in components.
Thales has identified the following priorities for in-car system security:
- Internal components, such as the most critical ECUs of the system (engine controller, etc.), must be protected from DoS[3] attacks via the vehicle’s external interfaces, particularly the onboard diagnostics (OBD) port used by garages and the intrusion detection/prevention IDS/IPS systems.
- Access to the system via the OBD port must require mutual authentication using X.509 certificates.
- Internal components must have authentication mechanisms using a robust encryption algorithm, such as a MAC algorithm. This solution makes it impossible to clone an ECU with malevolent code.
- The software and other applications on the ECUs must be electronically signed using an encryption algorithm such as RSA 2048, combined with an HSM (Hardware Security Module) to protect the private key.
- The most sensitive data, particularly the vehicle’s secret data and the user’s private data, should be encrypted using a robust algorithm, such as AES 256.
Find out more:
The right connections in Issue 5 of Innovations magazine (April 2016)